


Nancy Gohring, writing for InfoWorld, delivered a misleading report yesterday on a Mac security exploit contest held at the CanSecWest conference in Vancouver, BC.
In her defense, it appears likely that Gohring did not write the headline for her InfoWorld article, which described the contest winner as being “able to remotely break into a Mac as part of a contest designed to illustrate security flaws in OS X.” That part was simply wrong.
Whoever did write the headline must have been smoking weed in celebration of 4/20, because Gohring’s article clearly described a local exploit. There’s a big difference between the remote exploits that made Windows infamous for its insecurity and a local exploit of an application.
Gohring reported that “contestants were invited to try to access one of two Macs through a wireless access point while the Macs had no programs running. No attackers managed to do so, and so conference organizers allowed participants to try to get in through the browser by sending URLs via e-mail.”
Opening an email URL that exposes a security flaw in Safari is both news to report and a problem for Apple to tackle, but reporting it as a remote exploit is inaccurate, irresponsible, and sloppy journalism, particularly for IDG's InfoWorld, which purports to be an authority on computing.
Gohring's Mac Security Myths.
Beyond the glaring error of conflating a remote exploit with something that requires a concerted effort between a user acting locally on the machine and an outside party, Gohring's article perpetuated a number of myths about Mac security.
Gohring quoted Dragos Ruiu, the principal organizer of the security conference, as saying, “You see a lot of people running OS X saying it's so secure, and frankly, Microsoft is putting more work into security than Apple has.”
Of course, the reason why Microsoft has been forced to ‘put so much work into security’ is because of the infamous reputation the Windows platform has earned as a security nightmare. Microsoft was entirely blind-sided by the Windows security crisis, and was forced to attack its security problems out of embarrassment.
Microsoft’s Security Embarrassment.
Microsoft originally designed Windows to work in isolated office environments where there were few nefarious threats present. Mac OS X is based on a Unix foundation, which grew a hardened security callous along with development of the Internet. Unix security has been exhaustively researched by experts for decades.
Until just a few years ago, Microsoft shipped every copy of Windows wide open and listening to various ports for local network broadcast traffic. That's fine if a PC is being deployed as a test server on a chatty LAN Manager network, exchanging files with other PCs via Microsoft's insecure, proprietary SMB protocol. However, give it access to the Internet and it will be relaying spam in a matter of minutes.

Microsoft's applications, from its IE browser to Outlook mail, appeared to be designed specifically to accept and spawn malicious viral spores, and famously dragged Windows systems into one massive security crisis after another.
The vast majority of the world's spam is being distributed by Windows PCs serving as botnets, and Consumer Reports described Windows' antivirus/malware/spyware mess cleanup as a $9 billion problem.
Mac OS X and Security.
In contrast, there are currently zero real viruses for Mac OS X. It's not that it is impossible to infect or exploit a Mac, it's that Apple hasn't shipped millions of Macs listening wide open for commands to act upon, or shipped a web browser designed to naively run programs like Microsoft's ActiveX did, or installed an email program designed to automatically run commands that arrive as attachments as Outlook did.
 Given Microsoft's nearly complete lack of regard for security prior to about 2003, it's more than a little suspicious for a so-called security expert like Ruiu to inflate an obscure local vulnerability in Safari into the scale of the gross incompetence and negligence demonstrated by Microsoft over the previous decade.
Given Microsoft's nearly complete lack of regard for security prior to about 2003, it's more than a little suspicious for a so-called security expert like Ruiu to inflate an obscure local vulnerability in Safari into the scale of the gross incompetence and negligence demonstrated by Microsoft over the previous decade.It's also bizarre for Ruiu to backwardly complement Microsoft for solving some of its own problems while also dragging in a tired allusion to Artie McStrawman, the fanciful character who not only thinks Mac OS X is invulnerable to security issues, but also writes all those angry letters to Dvorak insisting it.
The Mac Minority Malware Myth
Gohring also repeated another myth in stating, “Macs haven't been targets for hackers and malicious code writers nearly to the degree that Windows machines have historically. That's in part because there are fewer Macs in use, thus making the potential impact of malicious code smaller than on the more widely used PCs.”
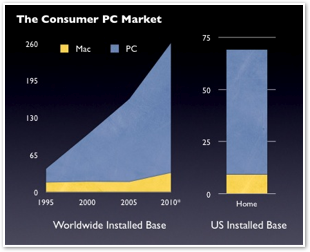
And while it's true that Macs make up only a small 2% of all the PCs sold worldwide, it's also true that Macs are commonly more valuable targets regardless of their distribution density. Further, Macs are not evenly distributed around the world.
For example, many schools are full of Macs; if they were easy targets because of wide open security flaws, school populations would see problems with Mac viruses. They do not. There are no real Mac viruses.
In Apple's target markets of home, education, and pro users in the US, Macs not only make up a significant proportion of the installed base of PCs in actual use, but also sit in affluent households which suggest prime targets. Still, malware and real world exploits are simply not common and virus plagues are nonexistent.
Do Apple's online Stores--and in particular the iTunes Store--all of which run WebObjects on Mac OS X Server on Xserves, ever suffer from security exploit attempts? Of course they do! We know the iTunes Store is under regular assault, because Apple has to regularly issue various fixes for iTunes.
The idea that Macs are not targets for hacking because there are not enough of them installed is laughable.
The reason why millions of botnet Windows PC are sending out spam is not because there are so many PCs, but because Windows security has been so bad for so long that all those millions of PC are easy targets to exploit. Simply plugging in a new PC to the open Internet will result in a rapid remote exploit of the machine within an hour.
For many years there have been millions of home routers running BSD and Linux, and PBXs running OS/2, and they aren't all virus ridden nightmares that spew spam from every pore. It's not the quantity of machines that makes exploits easy, it's the quality of the security on them.
Any security expert who is confused on that subject really needs to inform themselves better. IDG's InfoWorld is doing the world a disservice to offer up such rubbish information on the subject. Perhaps it should be rebranded as ConjectureWorld.
Corvettes aren't popular targets for theft because they are ubiquitous but rather because they are valuable. Similarly, if it were easy to remotely exploit Macs, they would offer hackers valuable targets both in environments where Macs are plentiful such as education, as well as sites where Macs are high profile goldmines, such as the iTunes Store servers.
Why Macs Aren’t Sending You Spam
Macs are not magically immune from security issues. The reason there are no viruses and very little malware for the Mac platform is a combination of several factors:
-
•Apple makes responsible efforts to design security into its products. Microsoft has a proven a track record of not taking security seriously over the last decade.
-
•When it discovers problems, Apple has taken prompt steps to solve the issues. That includes building a simple, automated Software Update system that helps users keep their machines up to date. Microsoft's update system is annoying and problematic, and tries to trojan in a DRM system with Windows Genuine Advantage.
-
•Mac OS X's core software draws from the security experience of the open source community. Windows is closed and proprietary to the core, hiding behind obscurity for its security. Unfortunately, that only makes potential exploits harder to find by security researchers; it does not stop malicious attempts to attack systems.

-
•Apple has opened the source of potential exploit vectors such as its Bonjour network discovery code, allowing security researchers searching for flaws open access to its mechanisms.
-
•Macs users have a community that recommends good software. In the Windows world, software comes in a wide range of quality and users are commonly not very selective or informed about what they install.
The real myth that Ruiu's CanSecWest Mac exploit contest demonstrated to be a fallacy is the idea that elite hackers attack systems for reputation and glory.
Simply offering fame and the new laptops as prizes generated little interest, according to a Security Focus report. It wasn't until Ruiu arranged to up the ante to $10,000 and lower the security threshold to involve a locally opened URL that the prize was awarded.
Listen up security pundits: hackers aren't after fame, they're exploiting security systems for money. As with any business, the easiest route is always to target the low hanging fruit first. In the computing world, that means exploiting PCs running Windows, not because they are common but because they offer an easy exploit for something of value: a way to send spam.
Like reading RoughlyDrafted? Share articles with your friends, link from your blog, and subscribe to my podcast!
Next Articles:
This Series

Haloscan Q107
InfoWorld Publishes False Report on Mac Security
Saturday, April 21, 2007

Ad






 Bookmark on Del.icio.us
Bookmark on Del.icio.us Discuss on Reddit
Discuss on Reddit Critically review on NewsTrust
Critically review on NewsTrust Forward to Friends
Forward to Friends
 Get RSS Feed
Get RSS Feed Download RSS Widget
Download RSS Widget





